Cryptocontainer vulnarabilities for remote attacks
-
At present, cryptocontainers are used to store confidential information both on user’s PCs and in corporate environment of businesses and institutions; they can be created with almost any encrypting software. Cryptocontainers are so widespread because they are convenient in handling encrypted files and offer opportunity to implement on-the-fly encrypting.
- a file manager
- a manager of open windows, tasks run, active processes
- services and autoload control
- remote registry control
- program installation/uninstallation
- capture of remote machine control using VNC technology
- remote screenshot taking
- interception of mic sound and built-in/external camera video etc.
 Nonetheless, only a few users realize how vulnerable files in a cryptocontainer become after the latter is mapped as a logical drive of the operational system, and how easily they can be stolen. This is why we have written this article, where we are going to demonstrate on a specific example how to steal information from a cryptocontainer created by means of iconic for RuNet (and others) TrueCrypt encrypting application. However, the same situation is true for any other software, which allows to create cryptocontainers and has no additional functions for protecting encrypted data they store.
Nonetheless, only a few users realize how vulnerable files in a cryptocontainer become after the latter is mapped as a logical drive of the operational system, and how easily they can be stolen. This is why we have written this article, where we are going to demonstrate on a specific example how to steal information from a cryptocontainer created by means of iconic for RuNet (and others) TrueCrypt encrypting application. However, the same situation is true for any other software, which allows to create cryptocontainers and has no additional functions for protecting encrypted data they store.
Let’s consider the following example. We assume that an AAA company stores sensible information on its server (using for the purpose an ordinary PC); some employees have access to the information. Confidential files are stored in a cryptocontainer created with TrueCrypt. To enable certified employees to work with the information during their working day, the cryptocontainer is mounted (e.g. by a system administrator) in the beginning of the day and demounted in the end. Executives of the company are firmly convinced that their confidential files are secure because they are stored encrypted in a cryptocontainer. To realize the danger threatening to the company, let’s assume we are BBB - a dishonest rival company eager to seize confidential information of AAA. We can implement the idea in some stages: 1. Download DarkComet RAT. This is the utility software for hidden remote administration, which has been developed officially to provide legitimate remote system control. We do not know whether the intentions of J.-P. Lecier (DarkComet’s developer) were really pure. Maybe he, just like Albert Einstein who could not imagine that the first application of his invention - nuclear energy would be an atomic bomb, also could not suppose that, in a short time, his product would be effectively used by hackers worldwide, and the Government of Syria would apply the program against its opposition in a Syrian conflict. DarkComet features:
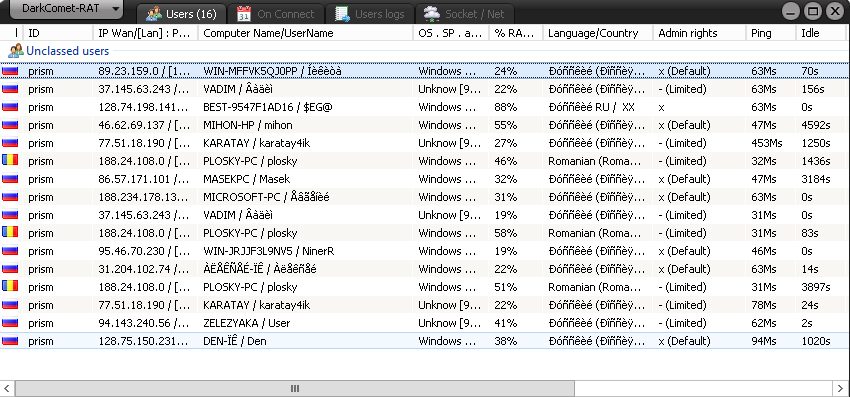 2. Once the utility is downloaded and installed, you need to arrange hosting to upload files from a victim’s PC.
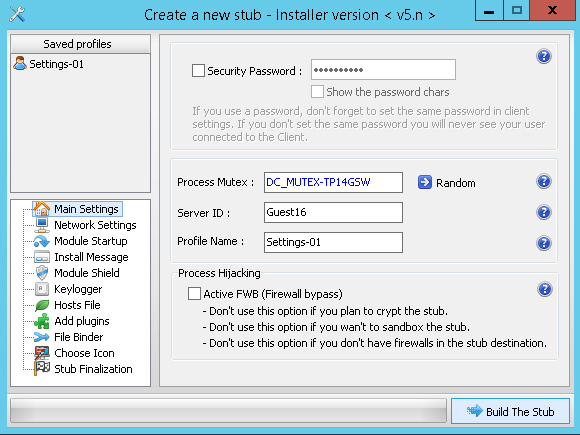
3. By means of DarkComet, we create an .exe file (stub), which will infect a victim’s PC (DarkCometRat > ServerModule > FullEditor). Then, we register the created host in Network Settings and specify other settings (see here for details). Or we can order to create such a file on a freelance marketplace (about 100 $).
2. Once the utility is downloaded and installed, you need to arrange hosting to upload files from a victim’s PC.
3. By means of DarkComet, we create an .exe file (stub), which will infect a victim’s PC (DarkCometRat > ServerModule > FullEditor). Then, we register the created host in Network Settings and specify other settings (see here for details). Or we can order to create such a file on a freelance marketplace (about 100 $).
 4. It is natural that the executable file created by DarkComet RAT is detected by antiviruses as malware. Therefore, to infect the victim computer, the file should be encrypted with an encryptor (can be ordered at 50-100$). The encryptor encodes the source file of the program and records in its beginning a code, which, being launched, will decode and run the main program. By encoding the program, the encryptor protects it against all major antiviruses and signature search techniques.
5. Make sure that antiviruses do not interpret the encrypted file as a virus. We can check it on VirusTotal.
In this article we do not provide the encrypted file directly, to avoid accusation of virus distribution. However, anybody who wants to make sure that antiviruses really do not interpret the encrypted file as a virus, can receive a link to the file from us and make sure himself by comparing hashsums in the video and on the file.
6. Now, we have to place our virus on the victim PC. There are many ways to do it.
For example, the computer can be infected via e-mail. During the working day, corporate mail boxes have dozens / hundreds of incoming e-mails. The huge correspondence does not allow each and every e-mail to be treated properly. The vast majority of employees handle the messages like pushing papers; it increases chances of successful attacks. When a violator sends a simple e-mail request, often, his victim fulfills the demand automatically, unaware of what he is doing.
This is just one example. Also, one can apply other social engineering methods based on human psychology.
7. As soon as the virus gets to the victim PC and the executable file is opened, the violator has full access to the computer under attack. As you know, any application calling the encrypted file placed on a linked cryptocontainer receives its decrypted copy. The DarkComet file manager constitutes no exception, enabling us to copy any information from a cryptodisk.
4. It is natural that the executable file created by DarkComet RAT is detected by antiviruses as malware. Therefore, to infect the victim computer, the file should be encrypted with an encryptor (can be ordered at 50-100$). The encryptor encodes the source file of the program and records in its beginning a code, which, being launched, will decode and run the main program. By encoding the program, the encryptor protects it against all major antiviruses and signature search techniques.
5. Make sure that antiviruses do not interpret the encrypted file as a virus. We can check it on VirusTotal.
In this article we do not provide the encrypted file directly, to avoid accusation of virus distribution. However, anybody who wants to make sure that antiviruses really do not interpret the encrypted file as a virus, can receive a link to the file from us and make sure himself by comparing hashsums in the video and on the file.
6. Now, we have to place our virus on the victim PC. There are many ways to do it.
For example, the computer can be infected via e-mail. During the working day, corporate mail boxes have dozens / hundreds of incoming e-mails. The huge correspondence does not allow each and every e-mail to be treated properly. The vast majority of employees handle the messages like pushing papers; it increases chances of successful attacks. When a violator sends a simple e-mail request, often, his victim fulfills the demand automatically, unaware of what he is doing.
This is just one example. Also, one can apply other social engineering methods based on human psychology.
7. As soon as the virus gets to the victim PC and the executable file is opened, the violator has full access to the computer under attack. As you know, any application calling the encrypted file placed on a linked cryptocontainer receives its decrypted copy. The DarkComet file manager constitutes no exception, enabling us to copy any information from a cryptodisk.
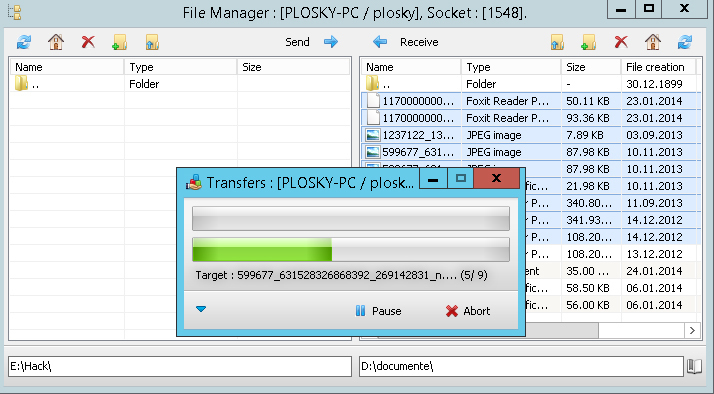 We shall obtain all files in a decoded form, available for reading and editing. Then, we can use them on our discretion. Here we can see another drawback of cryptocontainers: their big size of hundreds Mb facilitates the cybercriminal’s task to look for protected files.
That is all. The confidential information has been copied and compromised, a rival company can use it for its own ends. And the attacked organization has no idea of the data theft.
The process of stealing information from a cryptocontainer is clearly illustrated in this video:
We shall obtain all files in a decoded form, available for reading and editing. Then, we can use them on our discretion. Here we can see another drawback of cryptocontainers: their big size of hundreds Mb facilitates the cybercriminal’s task to look for protected files.
That is all. The confidential information has been copied and compromised, a rival company can use it for its own ends. And the attacked organization has no idea of the data theft.
The process of stealing information from a cryptocontainer is clearly illustrated in this video:
