Crypto containers vulnerabilities
One of the most convenient solutions to encrypt files is the creation of virtual encrypted volumes, which are also called crypto containers. However, not everyone is aware of the shortcomings of this method and that mismanagement of their use may do more harm than good. So in this article I want to talk about the crypto containers vulnerabilities and methods that allow dealing with them.

Intro. Briefly about crypto containers
In fact crypto container is a regular file, except it contains encrypted information, access to which is only available if you know a container password. Being mounted by encryption program crypto container is detected by the operating system as an additional local disk. You can copy and save any information on the disk, as well as work with encrypted files using any application. When working with the files encryption and decryption operations are performed “on the fly”, transparently to the user, which is very convenient.
Crypto container is a kind of digital safe on your computer to store confidential information. However, such disk has its "Achilles’ heel", or even several.
Crypto containers disadvantages
1. Crypto container can be removed by third parties
Without additional measures, the crypto container file can be seen, copied or even deleted by any user who has access to your computer. And if the copying doesn’t give the attacker or just curious absolutely nothing (all he’ll get is just a set of meaningless bytes), then removal can seriously harm and you’ll be left without all your encrypted information.
What is the solution? You can make a backup copy of the crypto container file as well as hide it from prying eyes and the operating system using special tools.
2. Accessibility through the network
When crypto container is mounted as a logical drive of the operation system it is possible to access it through the network. Even if the drive is not shared the ways to connect to it still exist if this drive is used in a network environment.
This also applies to remote access to your computer using TeamViewer, Radmin, VNC and other similar programs.
3. The lack of stealth
Crypto containers are large files on your computer's hard drive which occupy from hundreds of megabytes to tens of gigabytes. This clearly indicates that these files are crypto containers. Thus, the basic principle of protection by hiding the fact of protection is violated. And if someone is really interested in you and information on your PC, in practice, nobody will crack the crypto container as much easier in one way or another get your password.
4. Vulnerability in mount mode
In order to be able to work with the crypto container it must be connected (mounted). Up until the crypto container is not mounted, the information it contains cannot be read or modified.
However, when crypto container is connected it becomes vulnerable. For example, the crypto container has 1000 files, but you need only one of them *.doc. While you are working with this file, the other 999 files are also vulnerable to an attacker, for example, when implementing a remote attack that targets your computer.
Or, more likely, you’ll forget to dismount the crypto container and leave your PC unattended. In this case, anyone will be able to access your confidential data.
Therefore, when working with crypto container you should be very careful and connect it only if you need to work with encrypted files and disable immediately after the work is finished.
Alternative to crypto containers
CyberSafe Top Secret Software provides the ability to use the transparent encryption feature for folders on the user's local computer which supports “on the fly” encryption and doesn’t has the disadvantages which are peculiar to crypto containers.
First of all, you can encrypt any folder on your computer with any volume of data that will allow you to avoid creating large crypto containers.
No one except you will be able to delete the folder and encrypted files. The removal will be possible only if the password to your certificate is entered and the folder is enabled in the program:
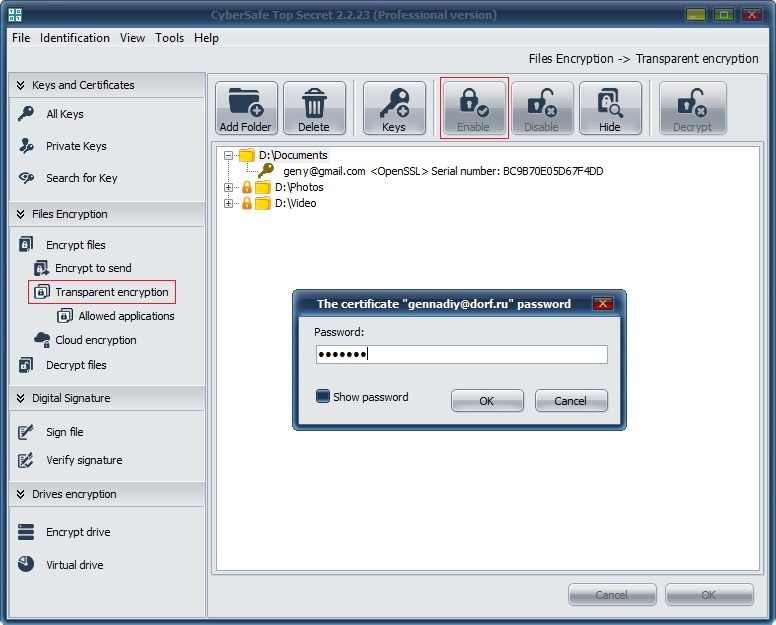 To eliminate the vulnerability which is peculiar to crypto containers mount mode (which is corresponds to the enabled folder) CyberSafe Top Secret has a Trusted Applications System that was added to program to strengthen its security.
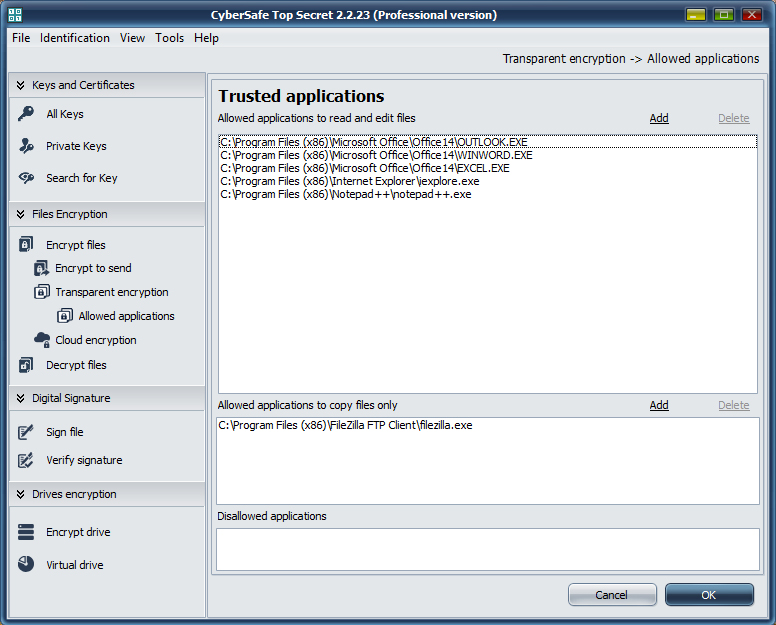
It allows you to create a list of trusted programs (for example Word, Excel, Outlook, Notepad++, Internet Explorer, etc.) that will be able to access your encrypted files, while the programs that are not trusted will not have access. In this way we limit access to confidential information for spyware, malware and other unwanted applications.
So if an attacker tries to gain your encrypted files when the folder is enabled (through the network or using remote access program) he won’t be able to get your data, because the files are only available for trusted applications.
To eliminate the vulnerability which is peculiar to crypto containers mount mode (which is corresponds to the enabled folder) CyberSafe Top Secret has a Trusted Applications System that was added to program to strengthen its security.
It allows you to create a list of trusted programs (for example Word, Excel, Outlook, Notepad++, Internet Explorer, etc.) that will be able to access your encrypted files, while the programs that are not trusted will not have access. In this way we limit access to confidential information for spyware, malware and other unwanted applications.
So if an attacker tries to gain your encrypted files when the folder is enabled (through the network or using remote access program) he won’t be able to get your data, because the files are only available for trusted applications.
 In addition, the program allows you to hide the encrypted files and folders. After using this option, the files are safely hidden from the operating system and other users, that provides an even higher level of protection for your data. The hidden elements remain invisible when booting the computer in safe mode and when being viewed via a remote administration program.
In addition, the program allows you to hide the encrypted files and folders. After using this option, the files are safely hidden from the operating system and other users, that provides an even higher level of protection for your data. The hidden elements remain invisible when booting the computer in safe mode and when being viewed via a remote administration program.
 Thus, by combining all of the above functions, you provide the highest level of protection for your valuable files.
Thus, by combining all of the above functions, you provide the highest level of protection for your valuable files.

 To eliminate the vulnerability which is peculiar to crypto containers mount mode (which is corresponds to the enabled folder) CyberSafe Top Secret has a Trusted Applications System that was added to program to strengthen its security.
It allows you to create a list of trusted programs (for example Word, Excel, Outlook, Notepad++, Internet Explorer, etc.) that will be able to access your encrypted files, while the programs that are not trusted will not have access. In this way we limit access to confidential information for spyware, malware and other unwanted applications.
So if an attacker tries to gain your encrypted files when the folder is enabled (through the network or using remote access program) he won’t be able to get your data, because the files are only available for trusted applications.
To eliminate the vulnerability which is peculiar to crypto containers mount mode (which is corresponds to the enabled folder) CyberSafe Top Secret has a Trusted Applications System that was added to program to strengthen its security.
It allows you to create a list of trusted programs (for example Word, Excel, Outlook, Notepad++, Internet Explorer, etc.) that will be able to access your encrypted files, while the programs that are not trusted will not have access. In this way we limit access to confidential information for spyware, malware and other unwanted applications.
So if an attacker tries to gain your encrypted files when the folder is enabled (through the network or using remote access program) he won’t be able to get your data, because the files are only available for trusted applications.
 In addition, the program allows you to hide the encrypted files and folders. After using this option, the files are safely hidden from the operating system and other users, that provides an even higher level of protection for your data. The hidden elements remain invisible when booting the computer in safe mode and when being viewed via a remote administration program.
In addition, the program allows you to hide the encrypted files and folders. After using this option, the files are safely hidden from the operating system and other users, that provides an even higher level of protection for your data. The hidden elements remain invisible when booting the computer in safe mode and when being viewed via a remote administration program.
 Thus, by combining all of the above functions, you provide the highest level of protection for your valuable files.
Thus, by combining all of the above functions, you provide the highest level of protection for your valuable files.
